Please visit our Contact Us page to inquire about any questions you may have regarding Cybersecurity or other services. Or visit our Contracting page to see info about Aloha Secure in the Government and State databases.

By reviewing your infrastructure's network architecture and controls, we identify where your business is most vulnerable to cyber threats and attacks. We have extensive practical experience (working in the DoD) managing complex security breaches, and respond promptly to reduce recovery time, costs and damage.

Aloha Secure has MANY methods to hack-proof your network & devices. We are Laser-focused on striking down targeted cyber threats - that make their way inside to attack the heart of the enterprise.
Aloha Secure is fully compliant and active with the Federal Government and listed in SAM database (sam.gov) as well as Federal Business Opportunities (fbo.gov). NAICs codes, PCS codes, Cage code, DUNS and other related info can be found in our Contracting page.
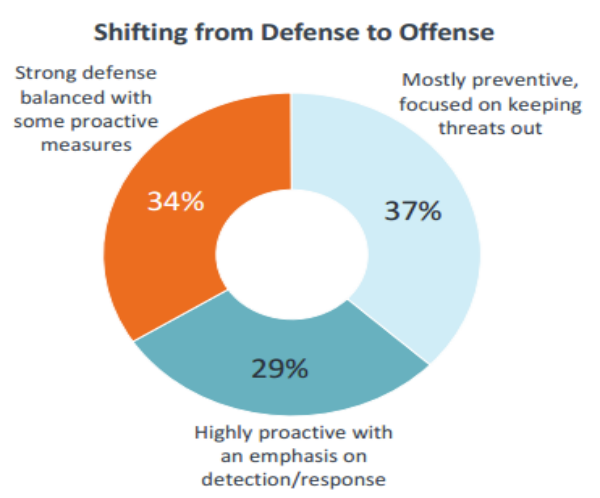
While traditional cybersecurity procedures have focused on creating impermeable systems, rapidly evolving threats have increased the need for a new perspective. Industry changes are calling for a more holistic look at cybersecurity.
Building an impenetrable "defense" is becoming less practical in comparison to a better focus on "offense", and the mentality of preventing all breaches is outdated. But a new, proactive approach combining technologies, procedures and education can help find problem areas before attackers discover them.
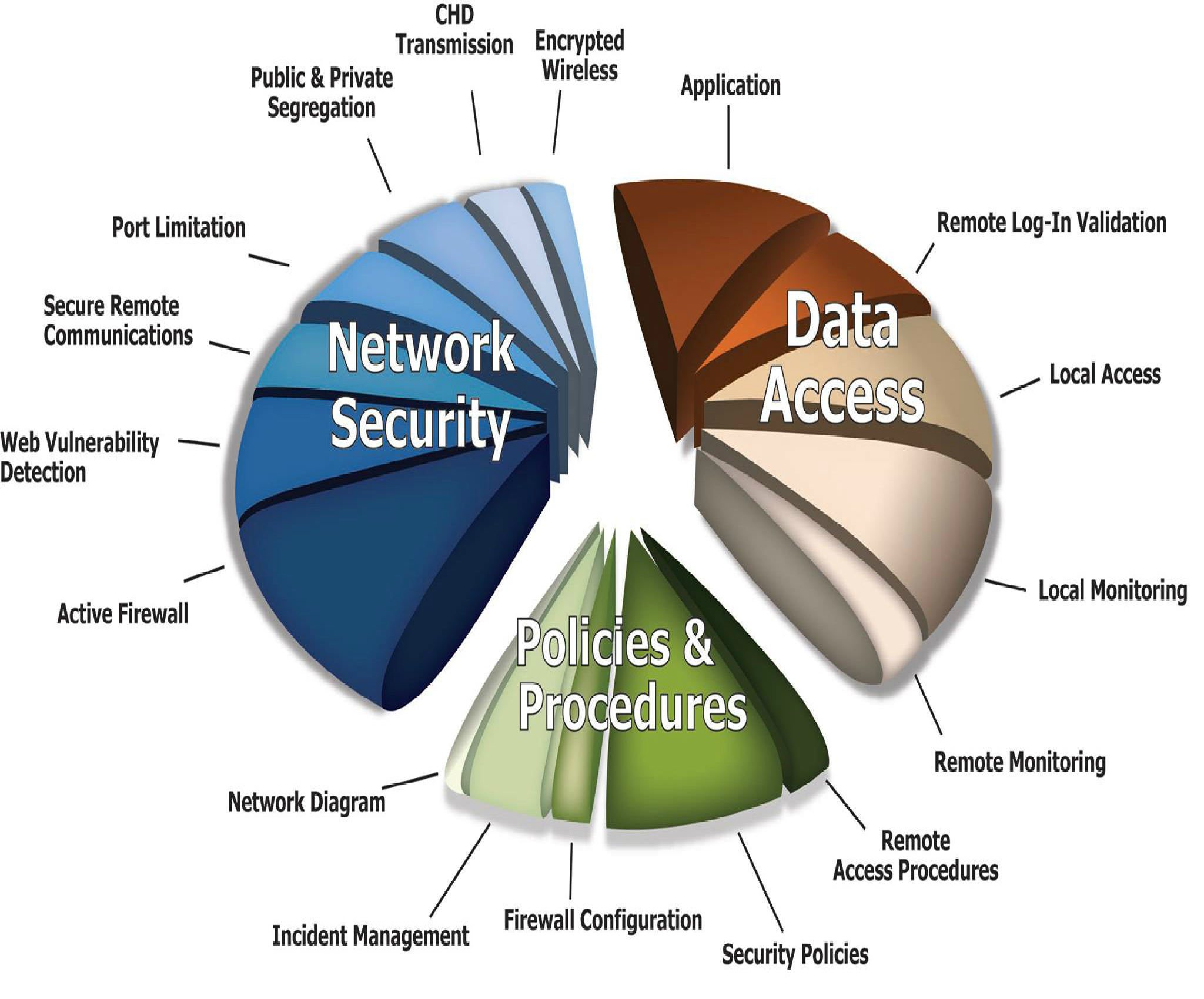
As you can see on the diagram to the right, there are many pieces to focus on in many different areas of the network to stay on top of best cybersecurity practices. Having a thorough understanding from each category - Network Security, Data Access, and Policies & Procedures is critical. Aloha Secure has vast amount of experience with many different vendors of networking equipment, appliances, Unix systems, Windows systems, servers, VM's etc. to be able to apply the best lockdown solutions possible.
We use Next-Generation Firewall technology - which includes application intelligence and adds device filtering functionalities such as application firewall using in-line deep packet inspection, an Intrusion Prevention / Detection System, routine network vulnerability scanning etc. Providing professional cyber support services that enable our customers to achieve information superiority. Prevent a critical network breach from happening before it's too late!

We have observed how many companies are only focusing on the types of attacks with which they are most familiar. Viruses and malware get the most attention compared to threats like dedicated denial of service (DDoS) and Internet of Things (IoT)-based attacks. Businesses are using more sophisticated systems, such as cloud computing and mobile devices, but are failing to defend against the security issues they may introduce.
While many companies have moved in the direction of cloud computing, mobile devices and other new technologies, it’s clear that a large number have failed to fully consider the corresponding security implications.
Aloha Secure goes above and beyond to meet all of these issues that companies face and provides outstanding service to create the best "hack-proof" environment from the workstation and end-user device level to the network SDP and beyond.
Please visit our Contact Us page to inquire about any questions you may have regarding Cybersecurity or other services. Or visit our Contracting page to see info about Aloha Secure in the Government and State databases.